Introduction
In the ever-evolving landscape of records security, professionals seek validation and expertise through certifications, with the Certified Information Systems Security Professional (CISSP) certification status out as a top achievement. This article: CISSP Domain Deep Dives- offers an in-depth exploration of each CISSP area, delving into key principles, contemporary challenges, and the critical position every area plays in fortifying organizational security.
Contents In Page
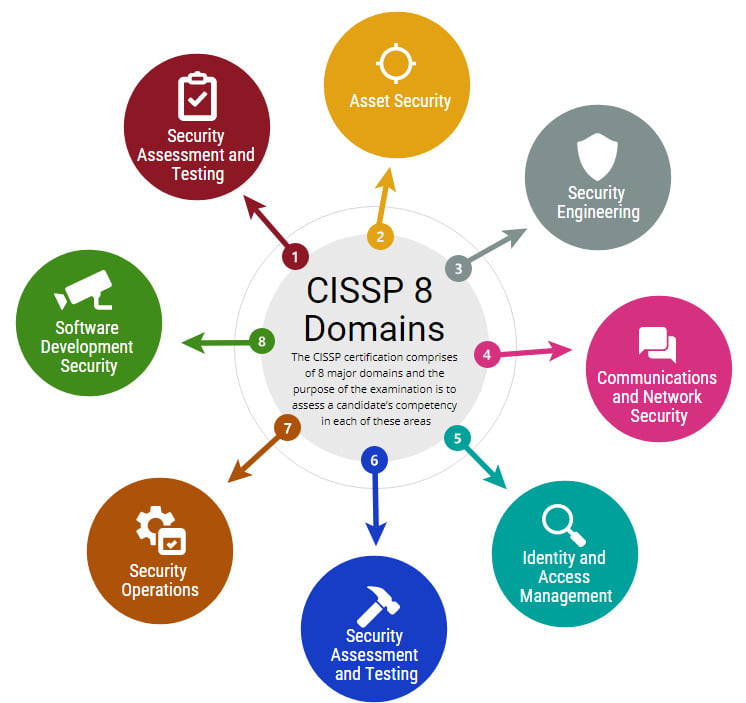
Toggle1. CISSP Certification Overview:

- The CISSP certification, governed by (ISC)², is a globally diagnosed general for validating know-how in statistics safety.
- The certification’s comprehensive nature spans multiple domain names, ensuring a holistic information of the field.
2. Information Security:
- Encompassing the safety of information assets, Information Security addresses unauthorized entry to, disclosure, disruption, change, or destruction.
- CISSP experts play a critical function in keeping the confidentiality, integrity, and availability of sensitive facts.
3. Cybersecurity:
- In the Cybersecurity domain, CISSP applicants navigate the dynamic landscape of safeguarding pc systems, networks, and virtual data.
- The emphasis is on understanding cutting-edge threats and staying beforehand with powerful mitigation strategies.
4. Network Security:
- Network Security, a important domain, makes a speciality of securing interconnected systems towards evolving threats.
- CISSP specialists make a contribution extensively to designing and keeping resilient community infrastructures.
5. Risk Management:
- Risk Management entails identifying, assessing, and mitigating dangers to data assets, enabling informed decision-making.
- CISSP-licensed individuals are adept at growing techniques to minimize ability damage.
6. Access Controls:
- This area delves into the concepts and implementation of Access Controls, figuring out who or what can get admission to precise sources.
- CISSP applicants explore fine practices in get right of entry to management, contributing to strong security postures.
7. Security Assessment:
- Security Assessment includes the ongoing evaluation of protection controls within statistics structures.
- CISSP specialists excel in carrying out thorough exams, figuring out vulnerabilities, and supplying remediation techniques
8. Security Policies:
- Foundational to a stable employer, Security Policies set hints for the proper use of facts structures.
- CISSP candidates apprehend the importance of well-defined and enforced policies.
9. Vulnerability Assessment:
- This domain specializes in systematically figuring out and prioritizing vulnerabilities within a machine.
- CISSP-licensed people conduct comprehensive vulnerability assessments, addressing potential weaknesses.
10. Incident Response:
- Incident Response prepares CISSP professionals to address protection incidents correctly, from identity to healing.
- Their activate reaction minimizes the impact of protection breaches on an organization.
11. Security Testing:

- Proactive Security Testing assesses the security capabilities of a system to discover vulnerabilities.
- CISSP professionals make sure structures are resilient to various forms of checking out, preemptively addressing weaknesses.
12. Cryptography:
- The area of Cryptography delves into the technology of steady conversation.
- CISSP applicants explore encryption algorithms, key management, and the application of cryptographic techniques.
13. Identity Management:
- Identity Management includes securing consumer identities and their get right of entry to to assets.
- CISSP experts contribute to organising strong identity control structures, making sure legal get admission to.
14. Security Operations:
- Encompassing every day sports, Security Operations are crucial for dealing with and responding to protection incidents.
- CISSP-certified individuals are nicely-versed in operational factors, contributing to ongoing safety resilience.
15. Business Continuity:
- Business Continuity planning guarantees critical features can hold in the event of a disruption.
- CISSP professionals make contributions to growing and retaining strong continuity plans, safeguarding companies.
16. Legal and Ethical Considerations:
- Exploring the felony frameworks and moral responsibilities in cybersecurity.
- CISSP applicants navigate the complicated panorama of legal and ethical concerns.
17. Security Governance:
- Security Governance involves organising a framework aligning protection strategies with organizational dreams.
- CISSP experts contribute to effective security governance, making sure strategic alignment.
18. Cloud Security:
- Addressing particular demanding situations in securing statistics and programs in cloud environments.
- CISSP-licensed people navigate complexities, making sure sturdy protection in cloud technology.
Conclusion:(CISSP Domain Deep Dives)
In studying the numerous CISSP domains, professionals emerge as adept at navigating the complicated and multifaceted demanding situations of statistics security. The CISSP certification stays a beacon for the ones devoted to safeguarding digital landscapes, gambling an quintessential function in fortifying agencies towards the evolving risk landscape. By exploring these domains and subpoints, CISSP professionals make a contribution appreciably to the resilience and safety of businesses global, making a lasting impact in the ongoing battle against cyber threats.